
AWS Attack Analysis & Threat Detection
Master AWS threat detection with hands-on CloudTrail analysis. Learn to identify attacks, investigate incidents, and defend cloud infrastructure against evolving threats.

In Partnership With:

Supporting Partner:
.png)
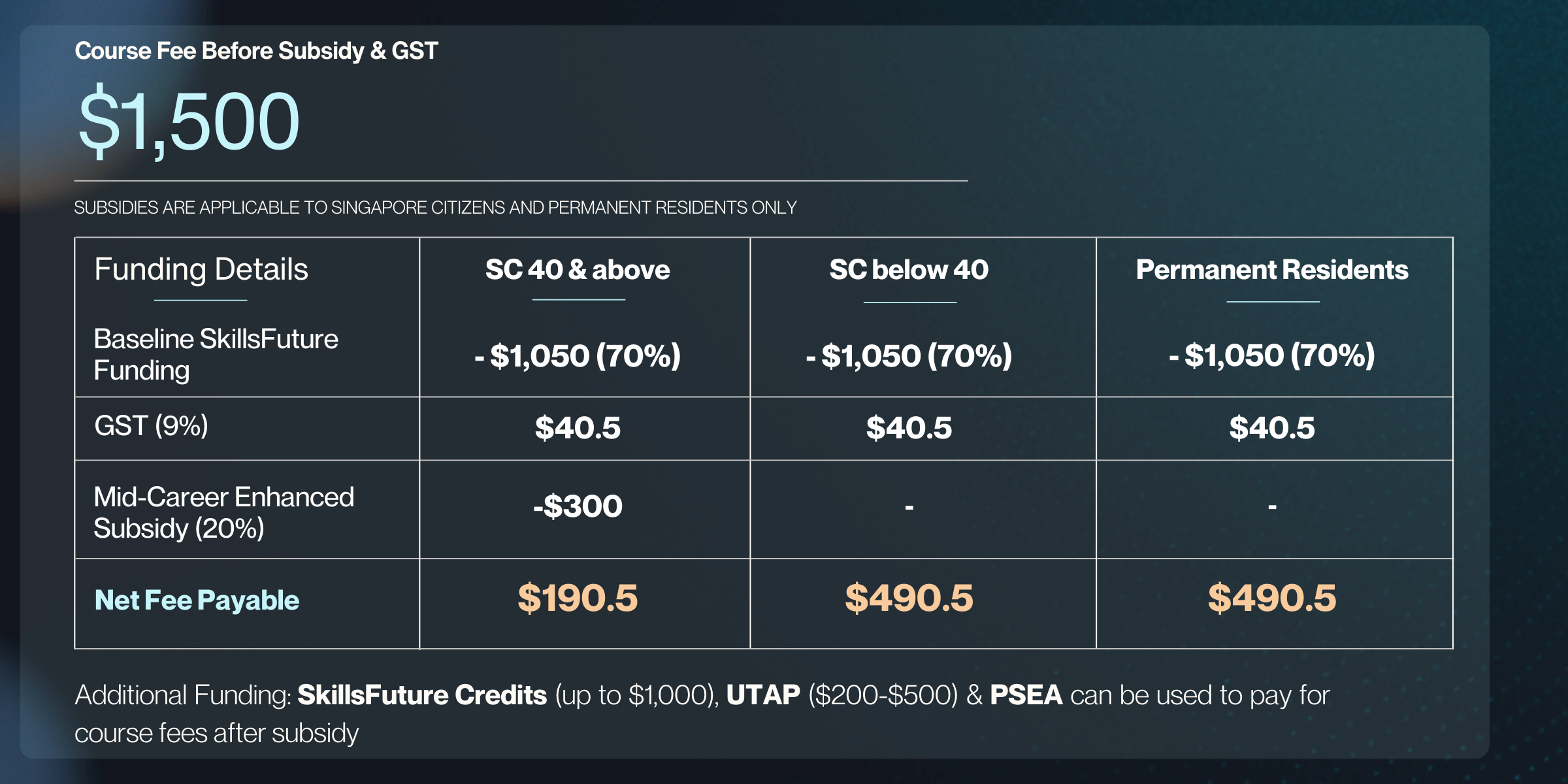
Course Fee
Full Course Fees
SG Citizen (aged 21-39) or PR
SG Citizen (aged 40 & above)
Full Fees
$19,500
$19,500
$19,500
SkillsFuture Funding
-
$13,650 (70% Subsidy)
$17,550 (90% Subsidy)
Total Nett Fee
$19,500
$5,850
$1,950
GST (9%)
$1,755
$526.5
$526.5
Total Fee Payable
$21,255
$6,376.50
$2,476.50
Additional Funding: SkillsFuture Credits (up to $500), UTAP ($200-$500) & PSEA can be used to pay for course fees after subsidy
Programme Fees & Funding
Learning Outcomes:
Who Should Attend
Security analysts, cloud security engineers, SOC teams, and IT professionals responsible for AWS security monitoring and incident response.
What You'll Learn
AWS security fundamentals, CloudTrail configuration and analysis, threat detection techniques, attack investigation methodologies, and practical threat hunting with real-world scenarios aligned to MITRE ATT&CK Framework.
Key Takeaways
Hands-on experience with AWS security services, ability to analyze CloudTrail logs for threats, understanding of common AWS attack vectors, and practical skills to detect and respond to cloud-based incidents.
Course Syllabus:
AWS Overview
Introduction to AWS core concepts and architecture.
Hands-on Configuration
Practical configuration of AWS services including IAM, EC2, Lambda, and S3. Provides fundamental knowledge before covering how these services are exploited by threat actors.
CloudTrail Fundamentals
Learn core concepts and functionalities of AWS CloudTrail for security monitoring.
Configuring CloudTrail
Master the process of setting up CloudTrail trails to capture relevant events and activities across your AWS environment.
- Become familiar with different attack scenarios
Log Interpretation
Develop ability to decipher CloudTrail logs to identify user activities, API calls, and resource changes.
Threat Detection
Learn to recognize indicators of compromise (IoCs) and anomalies within CloudTrail logs.
Advanced Analysis Techniques
Explore methods for extracting actionable intelligence from CloudTrail data.
- Become familiar with different attack scenarios
Common AWS Attack Vectors
Explore real-world attack scenarios including unauthorized access and data exfiltration.
Threat Actor Tactics
Analyze techniques employed by malicious actors to target AWS environments, aligned with the industry-standard MITRE ATT&CK Framework.
- Become familiar with different attack scenarios
Advanced Threat Hunting with CloudTrail
Analyze attacker methodologies and tactics captured in CloudTrail logs to understand adversary techniques, enabling proactive threat identification and countermeasures.
Practical Tips for Effective Threat Hunting
Learn proven best practices and actionable strategies to perform robust threat hunting with CloudTrail, ensuring efficient monitoring, detection, and response to evolving cyber risks.
- Become familiar with different attack scenarios
Training Schedule:
Day 1
AWS Fundamentals, CloudTrail Introduction, and Log Analysis foundations
Day 2
AWS Threat Landscape, Attack Detection, and hands-on investigation scenarios
Training Methodology:
Hands-On Labs
Practical exercises configuring AWS services and analyzing real attack scenarios
Live Demonstrations
Instructor-led attack simulations and CloudTrail investigation walkthroughs
Real-World Case Studies
Analysis of actual cloud security incidents and threat actor tactics
Interactive Discussions
Q&A sessions and group analysis of threat detection scenarios
- Become familiar with different attack scenarios
FAQs:
What are the prerequisites?
Basic understanding of cloud security concepts and AWS services is recommended.
Will I receive a certificate?
Yes, participants receive a certificate of completion from Centre for Cybersecurity Institute.
Is this course suitable for beginners?
This course is designed for security professionals with basic AWS knowledge. Some familiarity with cloud concepts is beneficial.
What tools will I need?
All lab environments and tools are provided. Participants need a laptop with internet connectivity.
- Become familiar with different attack scenarios
Secure Your Future
Find out more about how we can help you secure your future in cybersecurity


.png)