
Cyber Safety: Empowering Employees in Digital Defence
Keep your organisation protected with essential cybersecurity awareness knowledge.
In Partnership With:

In Partnership With:

Supporting Partner:
.png)
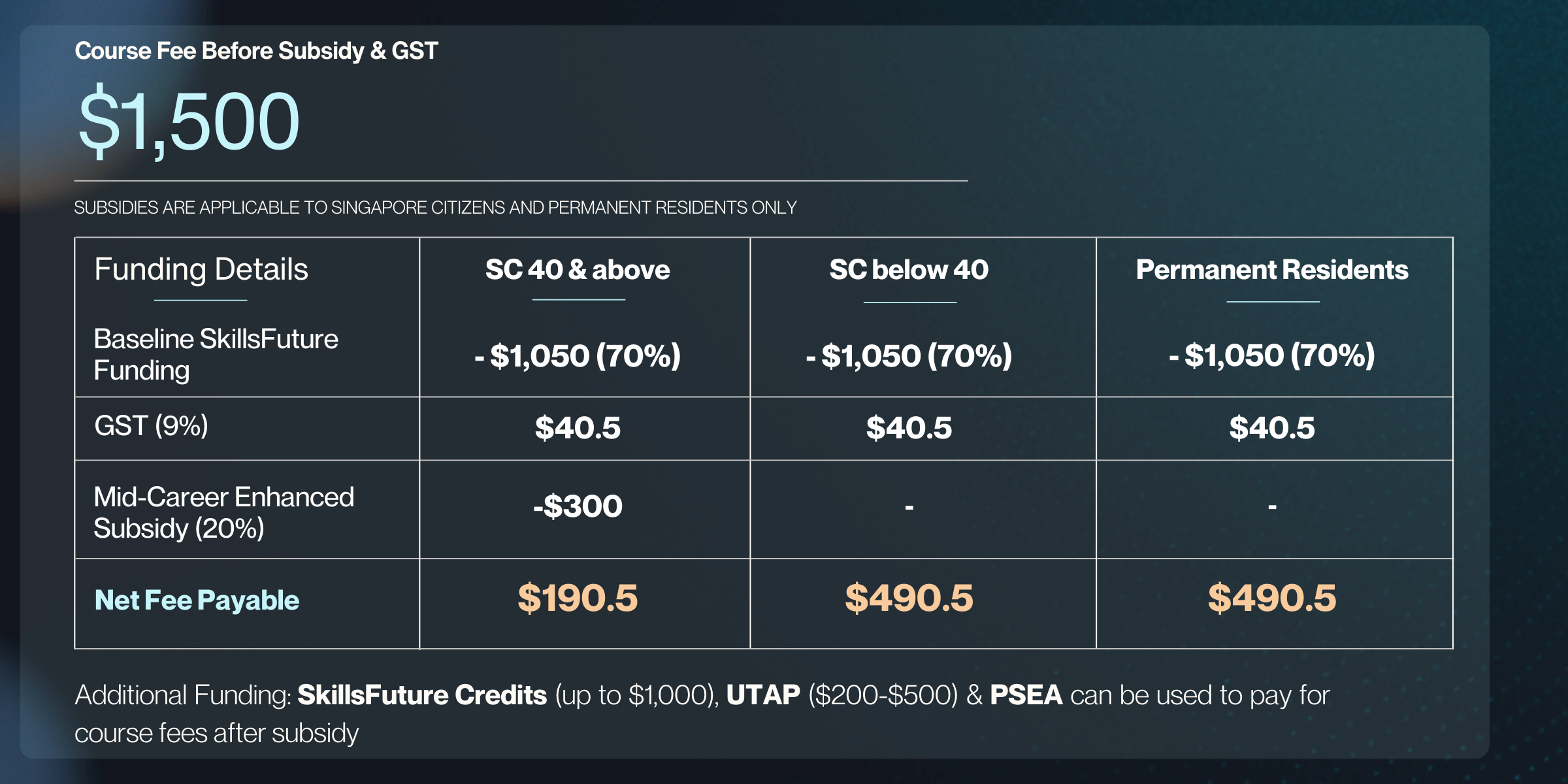
Course Fee
Full Course Fees
SG Citizen (aged 21-39) or PR
SG Citizen (aged 40 & above)
Full Fees
$19,500
$19,500
$19,500
SkillsFuture Funding
-
$13,650 (70% Subsidy)
$17,550 (90% Subsidy)
Total Nett Fee
$19,500
$5,850
$1,950
GST (9%)
$1,755
$526.5
$526.5
Total Fee Payable
$21,255
$6,376.50
$2,476.50
Additional Funding: SkillsFuture Credits (up to $1,000), UTAP ($200-$500) & PSEA can be used to pay for course fees after subsidy
Programme Fees & Funding
Learning Outcomes:
Organisation-specific Content
- Explanation and showcase of current cybersecurity initiatives by technical team
- Tailored to address specific cybersecurity risks and policies relevant to the organisation
- Meet internal audit requirements quickly & effectively
Interactive & Practical Learning
- Hands-on cybersecurity awareness activities
- Real-world scenarios to demonstrate risks
- Interactive discussion to contextualise and reinforce learning within teams
Facilitation
- Facilitator-led to ensure knowledge retention
- Emphasis of behavioural risks compromise organisational cybersecurity
- Learn up-to-date information from cybersecurity personnel
Comprehensive Course Materials
- Provision of cybersecurity quick reference guides for post-course reference
- Checklists for phishing email identification
- Tips for maintaining digital hygiene
Real-world Phishing Exercises
- Context-specific phishing demonstrations
- Post-training phishing exercise
Follow-Up Support
- Access to online tools and reading resources for continuous learning and reinforcement of cybersecurity best practices
Question text goes here
- Become familiar with different attack scenarios
Course Syllabus:
Chapter 01
Understanding Cyber Threats
Core Business Operations and Cybersecurity:
- Identify Core Business Activities Tied to Cybersecurity
- Assessment of Organisation’s Cybersecurity Knowledge
- Overview of Cybersecurity Threats
- Real-life Case Studies
IT Asset Management:
- Identify and list essential business assets.
- Best practices for asset management.
- Regularly updating the company's asset list.
Industry-Specific Cybersecurity and Privacy Regulations:
- Define your industry concerning cybersecurity.
- Recognize and comply with industry-specific regulations.
- Understand and protect sensitive business information.
IT Assets, Business Operations, and Regulations Synthesis:
- Identify key software and hardware.
- Assess IT asset downtime impact.
- Understand Service Level Agreements (SLAs) and potential breach impacts.
Business Resilience Planning:
- Develop a Maintenance Plan.
- Recognize incidental security features.
- Understand regulatory impacts and potential cybersecurity failures.
Financial Aspects of Cybersecurity:
- Business Continuity Planning (BCP) basics and importance.
- Disaster Recovery Plan (DRP) importance and formulation.
- Evaluate cybersecurity costs, risks, and risk assessment.
Corporate Cyber Hygiene:
- Introduction to cyber hygiene.
- Best practices for enhancing cybersecurity.
- Address human risk factors and fostering a cyber-safe culture.
Open-source Intelligence (OSINT)
- Phishing Awareness with live demonstration
- Types of Online Information
- OSINT Tools Overview
- Hands-on Exercise with Shodan
Linux Fundamentals
- Role in Modern IT Systems
- Overview of Linux Distributions
- Hands-on: Basic Command Practice
Password Security
- Importance of Password Hygiene
- Brute Force Attacks: Introduction, Demonstration, and Defence
- Password Best Practices
- Creating & Managing Passwords
- Using Password Managers
- Secure Password Sharing
MITRE ATT&CK Framework
- Real-World Use Cases
- Practical Application
CIA Triad Framework
- Introduction
- Real-World Case Studies
- Application in Business Cybersecurity
Cyber Response Playbook
- The Need for a Playbook
- Responding to Business Email Compromise (BEC)
- Creation of BEC Standard Operating Procedures (SOPs)
- Cultivating Cyber Vigilance
Email Cybersecurity
- Procedures for Inspecting Suspicious Emails
- Importance of Email System Hygiene
- Introduction to Secure Email Gateway (SEG)
- Protocols for Incident Reporting
Simulated Cybersecurity Threat Scenario
- Defence Strategy Against Simulated Cyberattacks
- Identifying and Addressing Breaches
- Investigation and Reporting Protocols
Chapter 02
Cyber Threats & Defence Techniques
Question text goes here
- Become familiar with different attack scenarios
Chapter 03
Question text goes here
- Become familiar with different attack scenarios
Chapter 04
Question text goes here
- Become familiar with different attack scenarios
Chapter 05
Question text goes here
- Become familiar with different attack scenarios
Training Schedule:
Tailored To Client
Question text goes here
Training Methodology:
Interactive Training
- Demonstration of real cybersecurity scenarios
- Continuous engagement and hands-on training
- Real-time simulation of cyber risks
Threat & Adversary Alignment
- Based on real-world cyber threats
- Understanding of latest risk vectors
- Practical and effective defence solutions
Question text goes here
- Become familiar with different attack scenarios
FAQs:
What is the minimum pax for this programme?
- A minimum of 20 pax is required for this programme
Who is this programme for?
- This programme is for organisations that would like to enhance their cybersecurity protection amongst non-technical staff members. It is suitable for both managerial and non-managerial positions.
Can this programme be conducted online?
- Yes, we can deliver the programme online if preferred by you.
Any Funding Available?
- This cybersecurity awareness training is HRDF claimable for Malaysian companies.
Question text goes here
- Become familiar with different attack scenarios
Quick Info
Programme Fee
Custom Pricing
Duration
Tailored To Client
Schedule
Tailored To Client
Teacher-to-Student Ratio
1:30
Delivery Mode
Online or On-site
View Course BrochureRegister NowBook Your SlotView BrochureView Brochure
Secure Your Future
Find out more about how we can help you secure your future in cybersecurity


.png)