
Network Security
Network Security
Explore, Exploit, Secure: Network Security Expertise.
In Partnership With:

In Partnership With:

Supporting Partner:
.png)
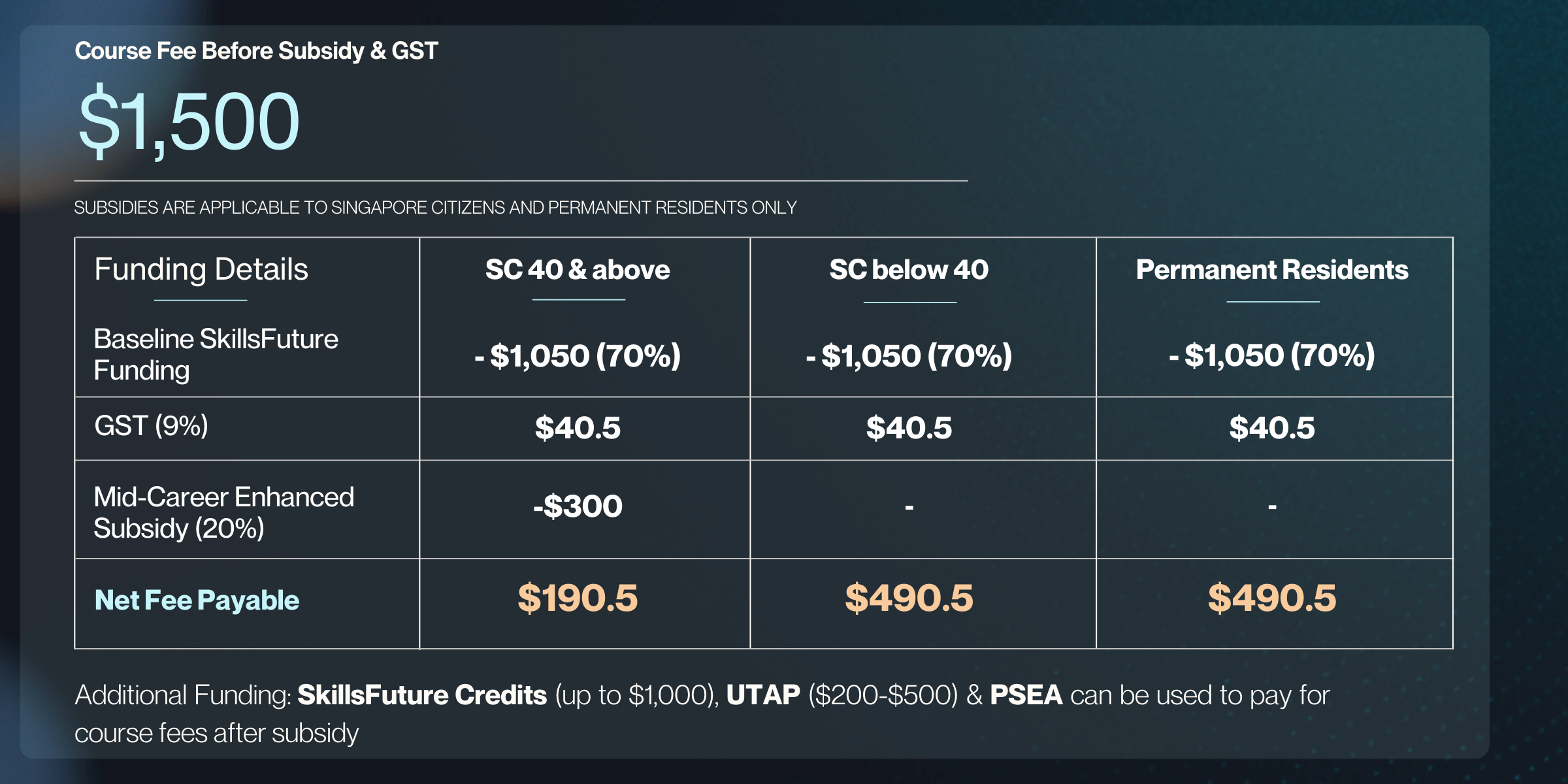
Course Fee
Full Course Fees
SG Citizen (aged 21-39) or PR
SG Citizen (aged 40 & above)
Full Fees
$19,500
$19,500
$19,500
SkillsFuture Funding
-
$13,650 (70% Subsidy)
$17,550 (90% Subsidy)
Total Nett Fee
$19,500
$5,850
$1,950
GST (9%)
$1,755
$526.5
$526.5
Total Fee Payable
$21,255
$6,376.50
$2,476.50
Additional Funding: SkillsFuture Credits (up to $500), UTAP ($200-$500) & PSEA can be used to pay for course fees after subsidy
Programme Fees & Funding
Learning Outcomes:
Participants will:
- Gain a deep understanding of network security principles and protocols.
- Develop proficiency in managing and securing Active Directory environments.
- Master PowerShell for Windows environment management and enumeration.
- Learn techniques for identifying and exploiting domain vulnerabilities.
- Understand encryption methods and their application in cybersecurity.
Course Syllabus:
Chapter 01
Advanced Networking
Network Security Fundamentals
- Principles of Network Security
- Packet Tracer
- Subnetting
Network Protocols
- DHCP
- SMB, SMB2
- LLMNR
- NBNS
Frameworks
- Enumeration
- Exploitation
- Pass-The-Hash (PTH)
Responder
- Collecting Information
- Cracking Passwords
Domain Setup
- Domain Installation
- Domain Services
Domain Protocols
- Kerberos
- LDAP
Domain Events
Chapter 02
Active Directory
Question text goes here
- Become familiar with different attack scenarios
PowerShell Commands
- PowerShell Text Manipulation
- PowerShell Event Logs
- PowerShell Enumeration
Chapter 03
PowerShell
Question text goes here
- Become familiar with different attack scenarios
Scanning
Enumerating
- Rpcclient
Exploitation
- Msfconsole
- Impacket
- CrackMapExec
Post Exploitation
- Mimikatz
- PSexec
- Golden Tickets
Domain Security
Chapter 04
Domain Exploitation
Question text goes here
- Become familiar with different attack scenarios
Encryptions
- Classic Encryptions
- Modern Encryptions
Chapter 05
Cryptography
Question text goes here
- Become familiar with different attack scenarios
Training Schedule:
Tailored To Client
Tailored To Client
Question text goes here
Training Methodology:
Apprenticeship-based Training
- Experience hands-on learning with our demonstration method on a virtual/host machine, ensuring immersive understanding.
- Our trainers prioritise showing over telling, explaining intricacies without relying on slides, offering direct engagement.
- Bridge your knowledge gap by connecting theoretical concepts to practical cybersecurity applications, enhancing career readiness.
Practice Labs
- Engage in repeated practice sessions to solidify and reinforce your understanding.
- Delve deeper with practice questions, encouraging students to explore interconnected topics and enhance comprehension.
- Stimulate critical thinking through challenge questions, prompting students to seek solutions and broaden their problem-solving abilities.
Assessment and Project
- Equip yourself with the expertise and tools essential for navigating corporate networks safely.
- Gain a comprehensive understanding of cyber-attacks to fortify your digital environment effectively.
- Broaden your horizon by familiarising yourself with diverse cyber-attack scenarios and their implications.
Question text goes here
- Become familiar with different attack scenarios
FAQs:
Question text goes here
- Become familiar with different attack scenarios
Quick Info
Programme Fee
Custom Pricing
Duration
5 Days (8 hours/day)
Schedule
Tailored To Client
Teacher-to-Student Ratio
1:30
Delivery Mode
On-site
View Course BrochureRegister NowBook Your SlotView BrochureView Brochure
Secure Your Future
Find out more about how we can help you secure your future in cybersecurity


.png)