
Cybersecurity Career Kickstart+
An 8-month, hands-on course designed to help mid-career individuals break into the cybersecurity industry.
In Partnership With:

In Partnership With:

Supporting Partner:
.png)
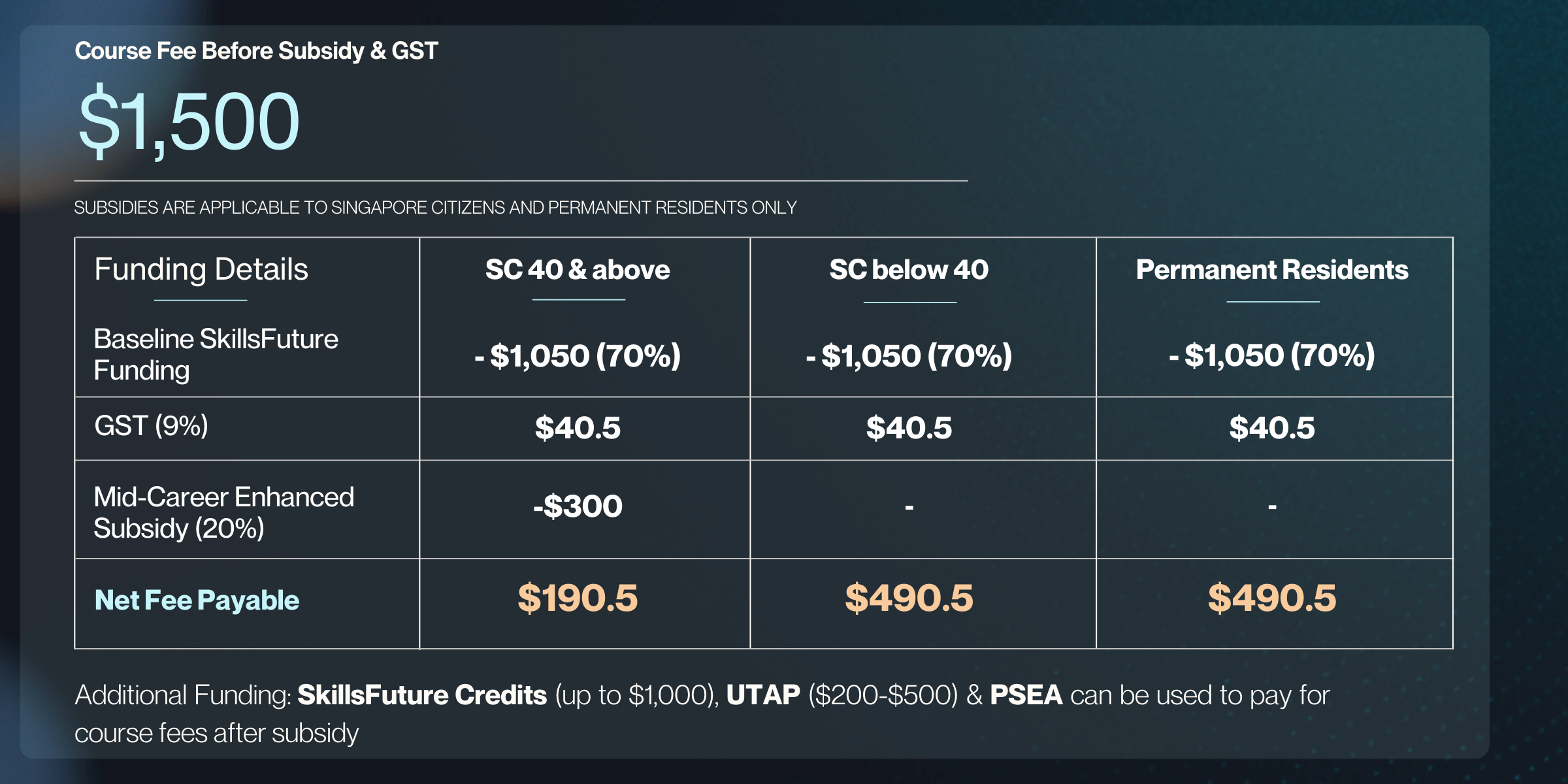
Course Fee
Full Course Fees
SG Citizen (aged 21-39) or PR
SG Citizen (aged 40 & above)
Full Fees
$19,500
$19,500
$19,500
SkillsFuture Funding
-
$13,650 (70% Subsidy)
$17,550 (90% Subsidy)
Total Nett Fee
$19,500
$5,850
$1,950
GST (9%)
$1,755
$526.5
$526.5
Total Fee Payable
$21,255
$6,376.50
$2,476.50
Additional Funding: SkillsFuture Credits (up to $1,000), UTAP ($200-$500) & PSEA can be used to pay for course fees after subsidy
Programme Fees & Funding
Learning Outcomes:
1. Foundational Knowledge:
- Acquire knowledge and tools for corporate network exploration
- Understand and defend against cyber-attacks
- Familiarise with various attack scenarios
2. Linux Proficiency:
- Utilise Linux command-line operations
- Comprehend Linux system configurations and graphical interface
- Implement automation in Linux
3. Programming and Scripting:
- Learn about Python variables
- Construct basic Python code
4. Security Operations Center (SOC) Insight:
- Gain a solid understanding of the SOC environment
- Develop practical skills in monitoring, log analysis, and event correlation
- Apply knowledge in real-time using a simulation environment
5. Network and System Configurations:
- Establish Domain roles and functionalities
- Configure rules and policies for DC, firewall, IDS, and IPS
6. Penetration Testing:
- Familiarise with the Penetration Testing Process
- Test and identify security weaknesses in systems
- Gather and enumerate vulnerabilities
- Exploit vulnerabilities to attack networks
- Implement steps to maintain access and pivot to other machines
7. Windows Forensics:
- Master digital investigation techniques through memory analysis and steganography to uncover hidden evidence in Windows environments.
- Develop forensic analysis skills from file system artifacts to network traffic, preparing you for professional investigations.
- Learn malware analysis and evidence carving techniques to identify and investigate cyber threats in Windows systems.
8. Cybersecurity Career Preparation:
- Master resume and CV writing for cybersecurity roles
- Hone interview skills tailored for cybersecurity positions
- Receive career coaching for a successful path in cybersecurity
Question text goes here
- Become familiar with different attack scenarios
Course Syllabus:
Chapter 01
Cybersecurity Fundamentals
Fundamental Concepts
- Basic Networking
- Remote Access
- Steganography
- Hash Encodings
Intro to Cybersecurity
- OSI Model
- Anonimity on the Network
- Basic Cyber Attacks
- Basic Network protocols
Linux Command-line
- Linux Distribution
- Basic Commands
- Permissions
- Text Manipulation
- Bash Scripting
- For loop, If statements, Functions,case
Networking
- Network Configuring and Troubleshooting
- Package management
- Install Deb packages
- Using APT
Intro To Python
- Variables
- Booleans
- List
- Dictionaries, Tuples
- Loops
Python Conditions & Functions
- Conditional Statements
- While and For Loops
- Working with Functions
Python Files I/O
- Python Modules
- Reading Files
- Writing Files
Intro to Linux
- Virtualisation
- Bridge vs NAT
- Linux Directories
- Linux Users
- Packages
- File and Text Manipulation
- Linux Scripting
Networking
- TCP/IP and OSI Model
- Network Routing Basics
- Network Protocols
- Remote Connection Protocols
- Wireshark
- Filtering and Parsing Traffic Logs
- Extracting Objects
Network Analysis
- Advance Wireshark
- Traffic analysis
- OS Fingerprinting
- Detecting Suspicious Traffic
- Filter packets
- File Carving
Network Attacks
- Network Scanning
- MitM
- LLMNR attack
- Offline, Online Password Brute Force
- Intro to Trojans
- Payloads: Reverse vs Bind
- Vulnerabilities on system
Chapter 02
Network Research
Question text goes here
- Become familiar with different attack scenarios
Windows Domain
- Install and configure windows server, ADDS
- Manage Domain Protocols and Policies
- Wireshark
- IP address subnetting
- Analyse Windows Events to monitor events and incidences on the DC
SOC Environment
- ELK deployment
- Beats deployment
- Identifying threats
- Data Aggregation
- Real-Time Monitoring
- Setting and Configuring pfsense rules
- Passing traffic
- Managing Network Security with IDS and IPS
Using SIEM
- Firewall Monitoring and management
- Install and configure firewall packages
- Web Gateway Filtering
- Vulnerability Assessment
Introduction to Threat Hunting
- Hardening Domain
- Setting up Open Source SIEM
- Deploying OSSIM
- Network and Host Monitoring and Logging
Chapter 03
Security Operations Centre (SOC) Analyst
Question text goes here
- Become familiar with different attack scenarios
Reconnaissance
- Monitoring Personal and Corporate Blogs
- Collecting Employees PersonalInformation
- Harvesting Organization Emails
- Shodan Search Engine
- Nmap Scanning
- Services Versions
- NSE Scripting
Enumeration
- DNS Enumeration
- FTP, SSH Enumeration
- SMB, MySQL Enumeration
- Network Traffic
- NSE Enumeration
- Vulnerabilities DetectionMethods
- Automating the Scanning
Exploitation
- Brute-ForcingServices
- Metasploit
- Working with Exploits
- Meterpreter
- Social Engineering
Post-Exploitation
- Configuring Payloads
- Analyzing Local Exploits
- Privilege Escalation
- Using the Meterpreter Modules
- Windows Linux PostExploitations
Chapter 04
Penetration Testing
Question text goes here
- Become familiar with different attack scenarios
Storage and File System Forensics
- Configuring Payloads
- Files and Disks
- File System Analysis
- Automatic Carving
- Metadata
- Steganography
System Artefacts and Configuration
- Artefacts
- Registry Analysis
- Windows Events
Volatile Memory Forensics
- Memory Analysis
Network and Malware Analysis
- Network Analysis
- Malware Analysis
Chapter 05
Windows Forensics
Question text goes here
- Become familiar with different attack scenarios
Training Schedule:
Week 1
- Basic Networking
- Remote Access
- Steganography
- Hash Encodings
Week 2
- OSI Model
- Anonymity on the Network
- Basic Cyber Attacks
- Basic Network protocols
Week 3
- Linux Distribution
- Basic Commands
- Permissions
- Text Manipulation
- Bash Scripting
- For loop, If statements, Functions, Case
Week 4
- Network Configuring and Troubleshooting
- Package management
- Install Deb packages
- Using APT
Week 5
- Intro to Linux (Ubuntu)
- Text Manipulation
- Services
- Scanning the network
Week 6
- Brute Force
- Fail2Ban
- Linux Scripting Recap
Week 7
- Linux Scripting for scanning
- Linux scripting to analyse files
Week 8
- Scripting - If conditions
- Scripting - functions
- Scripting - case
- Scripting to check password strength, malicious hash probability
Week 9
- Diving into packets - wireshark
- Local Network Attack - mitm
- Local Network Attack - llmnr
- VPN, Proxy and TOR
- Intro to Trojans
- Vulnerabilities on system
Week 10
- Install and configure windows server, ADDS
- Manage Domain Protocols and Policies
- IP address subnetting
- Analyse Windows Events Log
- Monitor events and incidences on the DC
Week 11
- Wireshark Analysis on SOC
- IDS and IPS Configuration
- Snort Installation and Rules Setting
Week 12
- Firewall Monitoring and management
- Install and configure firewall packages
- Web Gateway Filtering
- Vulnerability Assessment
Week 13
- ELK deployment
- Beats deployment
- Identifying threats
- Data Aggregation
- Real-Time Monitoring
- Setting and Configuring pfsense rules
Week 14
- Hardening Domain
- Setting up Open Source SIEM
- Deploying OSSIM
- Network and Host Monitoring and Logging
- SMB protocol and security issues
Week 15
- Backdoor with Netcat
- Domain Attacks, Monitoring
- Incidence Responding
Week 16
- Variables, Strings, Integers
- Booleans
- List
- Dictionaries, Tuples
- Loops
- Basic Python Scripting
Week 17
- Conditional Statements
- While and For Loops
- Working with Functions
- Python Modules
- Reading Files
- Writing Files
Week 18
- Monitoring Personal and Corporate Blogs
- Collecting Employees Personal Information
- Harvesting Organization Emails
- Shodan Search Engine
- Nmap Scanning
- Services Versions
Week 19
- Using NSE Scripts
- DNS, SMB, FTP, SSH, MYSQL Enumeration
- Network Traffic
- NSE Enumeration
- Vulnerabilities Detection Methods
- Automating the Scanning
- Brute-Forcing Services
- Metasploit
- Working with Exploits and other databases
- Meterpreter
Week 20
- Bind and Reverse Shell with Netcat
- Payloads and creating payloads
- Msfvenom
- Payloads Delivery
- Privilege Escalation
Week 21
- Post Exploit Linux
- Post Exploit Windows
- Cracking Windows password
- Automate msfconsole with rc script
Week 22
- OSINT with google and shodan
- Shodan on linux
- Bypass with Windows ISO and Kali
- Social Engineering and tools
- Intro to Web app hacking
2 x Weekdays Per Week (7 pm - 11 pm), 1 x Weekend Per Week (1 pm - 5 pm).
Question text goes here
Training Methodology:
Apprenticeship-based Training
- Experience hands-on learning with our demonstration method on a virtual/host machine, ensuring immersive understanding.
- Our trainers prioritise showing over telling, explaining intricacies without relying on slides, offering direct engagement.
- Bridge your knowledge gap by connecting theoretical concepts to practical cybersecurity applications, enhancing career readiness.
Practice Labs
- Engage in repeated practice sessions to solidify and reinforce your understanding.
- Delve deeper with practice questions, encouraging students to explore interconnected topics and enhance comprehension.
- Stimulate critical thinking through challenge questions, prompting students to seek solutions and broaden their problem-solving abilities.
Assessment and Project
- Equip yourself with the expertise and tools essential for navigating corporate networks safely.
- Gain a comprehensive understanding of cyber-attacks to fortify your digital environment effectively.
- Broaden your horizon by familiarising yourself with diverse cyber-attack scenarios and their implications.
Question text goes here
- Become familiar with different attack scenarios
FAQs:
Do I need to have any programming knowledge to join the course?
- No prior programming or coding knowledge is needed. We teach all relevant programme skills, such as Python, during the course in the context of cybersecurity.
Are there grants available?
- Eligible candidates will receive between 70%-90% in SkillsFuture Subsidies.
- All Singaporeans aged 25 and above can use their $1000 SkillsFuture Credit from the government to pay for the Cybersecurity Career Kickstart+ course.
- UTAP & PSEA funds can also be used to pay for the Cybersecurity Career Kickstart+ course.
What if I cannot cope and want to drop out?
- We urge students to think twice before dropping out, as it impacts their progress. Our goal is to see every student graduate and secure a cybersecurity role. We're here to help you overcome challenges and adjust to your needs. If you're set on leaving, your trainer will work with a member of the student success team to assist you.
Can you guarantee that I will get a job?
- We do not guarantee any students that they have a 100% chance of securing a job. We provide you with the best opportunity to secure a career in the industry. Each individual has a unique situation and expectations of a cybersecurity career upon graduating. From our experience, some graduates turn down job offers due to personal preferences (e.g. shift work, salary requirements, etc) and take longer to find a role they are comfortable with.
What are the computer specifications I need for the course?
An Intel-based Windows or MacBook Pro laptop with the following specs:
- 6-core CPU
- x64-compatible 2.0 GHz CPU minimum or higher
- Intel i5 Gen 7 and up
- 16 GB RAM minimum
- 512 GB available hard-drive space
- Able to Support Hypervisor
- Laptop or stationary computer workstation. (Tablets / Surface Pro not suitable)
- Internet bandwidth - minimum base connection speed of 10 Mbps down/up is required.
What certifications do I get from the course?
- One 'Cybersecurity Career Kickstart+' Certificate from Ngee Ann Polytechnic
- Seven modular skills certificates from Ngee Ann Polytechnic
- One 'Certificate of Completion in Windows Forensics & Incident Response' from Centre For Cybersecurity Institute
- One "GIAC Certified Incident Handler (GCIH)" Examination Voucher (T&C Applies)
Question text goes here
- Become familiar with different attack scenarios
Quick Info
Programme Fee
$19,500 (Up to 90% Subsidy Available)
Duration
8 months, 333 hours (Part-time)
Schedule
2 x Weekdays Per Week (7 pm - 11 pm), 1 x Weekend Per Week (1 pm - 5 pm).
Teacher-to-Student Ratio
1:30
Delivery Mode
Online
View Course BrochureRegister NowBook Your SlotView BrochureView Brochure
Secure Your Future
Find out more about how we can help you secure your future in cybersecurity


.png)